SANS Holiday Hack Challenge 2019
KringleCon 2 - Obj 6
6) Splunk
Difficulty: 🎄🎄🎄 (3/5)Access https://splunk.elfu.org/ as elf with password elfsocks. What was the message for Kent that the adversary embedded in this attack? The SOC folks at that link will help you along! For hints on achieving this objective, please visit the Laboratory in Hermey Hall and talk with Prof. Banas.
| Professor Banas |
Hi, I'm Dr. Banas, professor of Cheerology at Elf University.
This term, I'm teaching "HOL 404: The Search for Holiday Cheer in Popular Culture," and I've had quite a shock!
I was at home enjoying a nice cup of Gløgg when I had a call from Kent, one of my students who interns at the Elf U SOC.
Kent said that my computer has been hacking other computers on campus and that I needed to fix it ASAP!
If I don't, he will have to report the incident to the boss of the SOC.
So we go and access the Splunk site to find it has a chat screen where we are already having a conversation with the SOC.
Alice Bluebird is ready to train us in Splunk by helping the SOC answer a few questions about the incident. She gives as some info about the attack, they are related to the RITA Zeek logs we analyzed before and the host's name is 'sweetums'
 |
| Chat with Alice |
Our goal is to find a message embeded in a file, the SOC has an archive of all the files related to the events available on a website.
So the answer for the first Training Question, What is the short host name of Professor Banas' computer?, can be answer by looking in Splunk for the hostname sweetums and see what users are related to it.
 |
| Search for users using the host 'sweetums' |
Prof. Banas user is 'cbanas', and is the user related to the host 'sweetums', so we have our first training answer.
Now we get a new question.
2. What is the name of the sensitive file that was likely accessed and copied by the attacker? Please provide the fully qualified location of the file. (Example: C:\temp\report.pdf)
 |
| Alice chat for Question 2 |
Alice gives us the next tip, Prof Banas is very close to Santa, so they were probably exchanging important information, we know from previus engagements with Santa that they most important data the North Pole manages is the Nice and Naughty list, so we see if we can find anything related to that.
 |
| A Draft for a Nice and Naught list was a parameter of a Get-Item PowerShell Commandlet |
We actually found a draft list for the Nice and Naughty that has been read by a very strange base64 coded powershell script, so this most be the file Question 2 is referring to.
After answering, Alice tells us that just looking for the string Santa will give us the answer.
 |
| Using Alice's Splunk Search |
Now we move to question 3.
3. What is the fully-qualified domain name(FQDN) of the command and control(C2) server? (Example: badguy.baddies.com)
Alice needs us to look for the FQDN of the C&C using the Sysmon logs in Splunk to determine where is the PowerShell connecting. She even provides a link to a blog about Splunk and Sysmon Search string to start our investigation.
 |
| Found FQDN of C&C |
And we have found the FQDN of the C&C to answer question 3 - 144.202.46.214.vultr.com
Now we move to Question 4
4. What document is involved with launching the malicious PowerShell code? Please provide just the filename. (Example: results.txt)
The chats start to get longer and very uncomfortable to cut and paste the images, so I'll just describe what Alice says.
Alice tells us to investigate where did the PowerShell came from and provides a search:
index=main sourcetype="WinEventLog:Microsoft-Windows-Powershell/Operational"
She wants us to look at the processes' PIDs and GUIDs but the exact process the information is not all there, we need to pivot on another field, time.
So I've come up with my own search to make the conversion from hex to dec and join the results, and instead of |revers I used |sort - _time because all habits don't die
index=main process_id=* user=*cbanas* | rename process_id AS pid | join pid max=0 [search index=main sourcetype=WinEventLog EventCode=4688 | eval ppid=tonumber(Creator_Process_ID,16), pid=tonumber(New_Process_ID,16)| table _time ppid Creator* pid New_Process_Name Process_Command_Line Process_Command_Line] | table _time ppid Creator* pid New_Process_Name Process_Command_Line | search New_Process_Name=*powershell* | sort _time
This gives us a list of PowerShell processes created and it's creator sort ascending by time, so the first time a powershell is executed is listed first, this happened 2019-08-25 at 17:38:35.
Following Alice's pivoting tip, we then look for a WINWORD process executed just before the powershell being spawned.
index=main sourcetype=WinEventLog EventCode=4688 New_Process_Name=*WINWORD* | eval ppid=tonumber(Creator_Process_ID,16), pid=tonumber(New_Process_ID,16)| table _time Process_Command_Line
And we find the most probable "document" that started the PowerShell - 19th Century Holiday Cheer Assignment.docm
5. How many unique email addresses were used to send Holiday Cheer essays to Professor Banas? Please provide the numeric value. (Example: 1)
Just by reading the question I know I have to build a search that looks for the strings "Holiday Cheer Essay" that have Professor Banas as the recipient. Luckily Alice gives us more sample searches.
This search gives us a count of 21 emails sent, and that's the right Answer.
The same search results gives us the answers for questions 6, and 7
6. What was the password for the zip archive that contained the suspicious file?
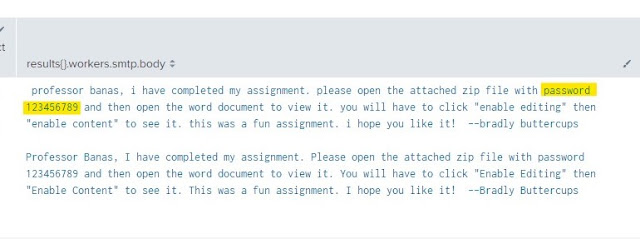 |
| Zip file password |
7. What email address did the suspicious file come from?
 |
| email address found |
And now for the challenge question...
What was the message for Kent that the adversary embedded in this attack?
Of course Alice still have tons of help to provide us
Alrighty, enough said... we need to look for a core.xml file, let's use a combination of the searches Alice gave us but including the string password to get files related to the email in question.
index=main sourcetype=stoq "results{}.workers.smtp.from"="bradly buttercups <bradly.buttercups@eifu.org>" password | eval results = spath(_raw, "results{}")
| mvexpand results
| eval path=spath(results, "archivers.filedir.path"), filename=spath(results, "payload_meta.extra_data.filename"), fullpath=path."/".filename
| search fullpath!=""
| table filename,fullpath
 |
| Direct Link |
 |
| File with the message. |
| There's the message and final Answer for the challenge. |
| Congratulations! |
Oh, thanks so much for your help! Sorry I was freaking out.
I've got to talk to Kent about using my email again...
...and picking up my dry cleaning.
I've got to talk to Kent about using my email again...
...and picking up my dry cleaning.








Comments
Post a Comment