*** DON'T TRY THIS AT HOME/WORK****
Today I got a wonderful Phisihng email, the attacker sent me a DHL bill for an account I don't have so that's the first red flag, then the attachment was an HTML instead of a PDF as stated in the email
So I decided to take a look...
I downloaded the attachment and took a pick form my WSL Linux console
Very interesting:
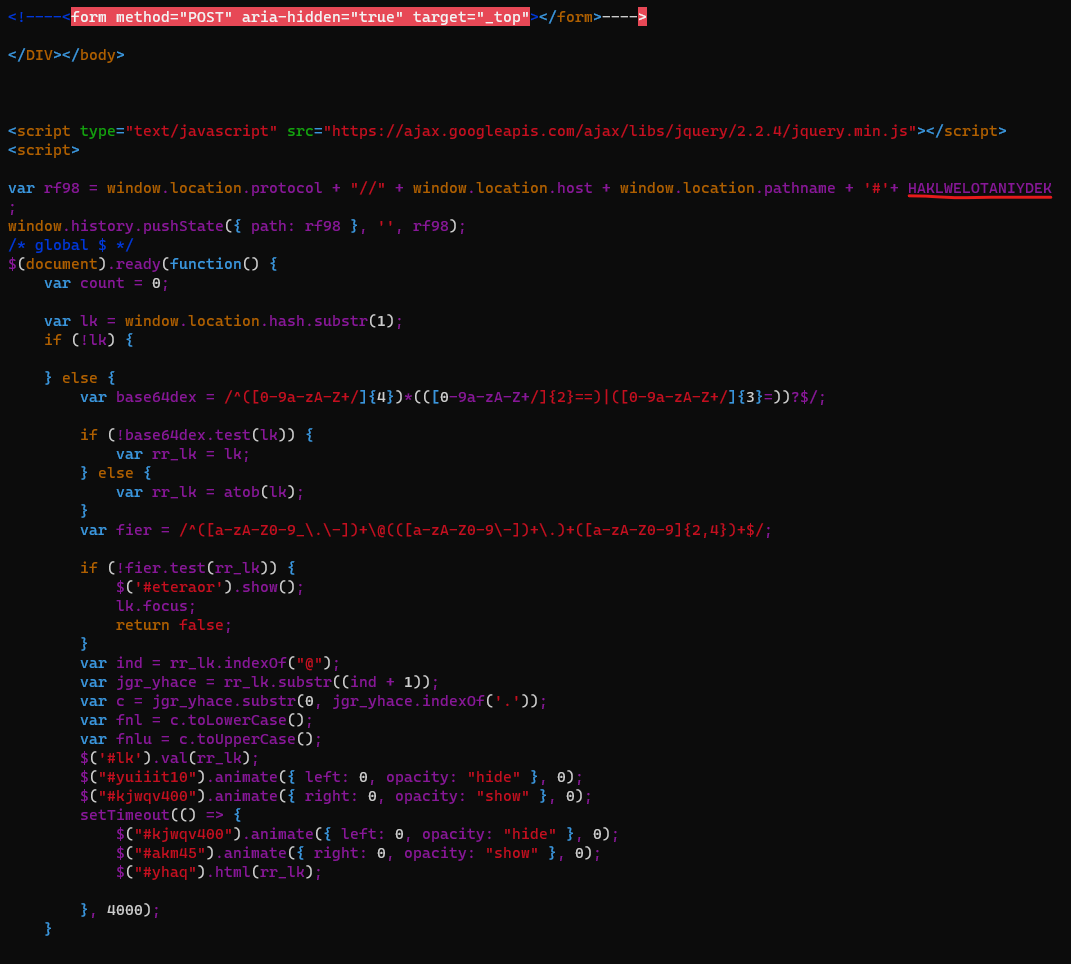
The HAKWELOTANIYDEK variable contains my email address
The Stivenkalvin variable has a base64 value that decoded becomes
hXXp://ocbpremium.org/app/loi1hn.php so this website has been probably hacked and now host this PHP creds collector.
BTW, I try putting HAKWELOTANIYDEK in Google translate and the best match was a romanization of Arab
When trying that URL we get redirected to office.com, probably because we don't have the right parameters to give the PHP, making people think this is a legit website.
With curl -L we can follow any redirects, HTTP code 302 indicates a redirection and the Location where are we going.
Now we have the rest of the base64 encoded JavaScript:
The atob() method decodes base64 to ASCII and document.write() populates the DOM document with the result loading all the code into the browser.
If we decode the base64 text we get HTML content with JavaScript that imitates a Microsoft login page, prepopulates the username with the value in the HAKWELOTANIYDEK, and even turns off autocomplete, no matter what you type for the password it will always return wrong password and send the information to their server.
Keeps replacing the URL on the browser with office.com with
atob("aHR0cHM6Ly9vdXRsb29rLm9mZmljZS5jb20vbWFpbC8")
QUICK UPDATE, the hXXp://ocbpremium.org/ is a fake website
The DNS is hosted by NameCheap 🚩🚩🚩🚩










No comments:
Post a Comment